Missed Part 1? Find it here.
Deciding on a BYOD Adoption Strategy
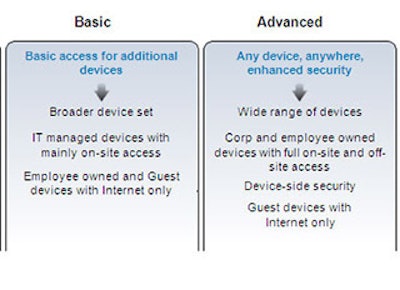
Different businesses will approach BYOD with different expectations across a spectrum of adoption scenarios. Every business needs a BYOD strategy, even if the intention is to deny all devices except IT approved and managed devices. Figure 2 shows a number of possible adoption scenarios into which most businesses fit.

Figure 2
Businesses within industries with high degrees of regulation, such as finance or secure government agencies, may need to take a restrictive approach with BYOD adoption to protect sensitive data. Devices may need to be tightly controlled and managed as in the traditional IT approach, which may still be valid in these instances.
For many companies, adoption will range from allowing a broader set of devices with restrictive access to applications to embracing BYOD in full, encouraging broad adoption of many or all device types and deploying security measures to enable access to a broad set of enterprise applications and data. In the broadest sense, some companies will adopt a “mobile first” strategy, whereby their own internal applications development will be prioritized on tablets and smartphones, seeking competitive advantage by leveraging the broadest set of productivity tools and devices.
Understanding where your business will fit now and in the future along the adoption spectrum is useful to prepare for security policies, entitlement, and overall strategy for the BYOD initiative.
Understanding Native, Browser, and Virtual Modes
Securing and preventing the loss of corporate data is a top concern when implementing BYOD. It is important to understand three possible application architectures and the trade-offs involved: native, browser, and virtual. These are shown in Figure 3.

Figure 3: Native and Virtual Modes
In native mode, applications running on the device communicate directly with the application server in the host data center (or cloud). Data may be exchanged and stored directly on the BYOD device. Typically the application performance and user experience are closest to the specific device; in other words, a business application functions much like any other application on the device. All the productivity benefits and device behavior are preserved and applications can be tailored to provide enhanced experiences.
A browser approach is increasingly being adopted for application access due to the ease of portability across devices and operating systems. Essentially any device with a standard HTML browser capability can be used to access the application. The disadvantages are that much like native mode, data may be exchanged and stored directly on the BYOD device, leading to security challenges and concerns about data loss. In addition, there may be some sacrifice of user experience.
To contrast, in virtual mode applications exist on the application server in the data center (or cloud) and are represented through a VDI client on the device. Data is not stored locally on the BYOD device. Only display information is exchanged and rendered on the BYOD device. While this method provides maximum data security, user experience may be a compromise due to the translation from an application server to the form-factor and OS native to the BYOD device. Early adopters of this approach have provided somewhat negative feedback.
It is important to make decisions about which mode, native or virtual, will be relied on for the application architecture. Many companies may use a hybrid approach, using native mode for many standard business applications and virtual mode for a subset of applications with stricter confidentiality or sensitive data requirements.
Have an Encompassing End User Agreement
Although not part of the network architecture, one area that must be well thought out prior to any BYOD implementation is the end user agreement (EUA). Because of the mixing of personal and corporate data, and the potential of having employee-owned devices being used for work, it is critical to outline policies up front and be sure to communicate these to employees in advance.
IT organizations need to familiarize themselves with laws, including the Computer Fraud and Abuse Act, the Wiretap Act, and Communications Assistance for Law Enforcement Act (CALEA).
What will company policies be? Will communications be subject to monitoring? Will policies apply to both corporate and personal? Areas to be addressed include (but are not limited to):
- Text messaging
- Voice calling
- Internet browsing
- Instant messaging
- GPS and geo-location information
- Applications purchased/installed
- Stored photographs and videos
- Device “wiping”
Keep reading here...























